Monday, August 30, 2010
How to find the IP address of the sender in Gmail
When you receive an email, you receive more than just the message. The email comes with headers that carry important information that can tell where the email was sent from and possibly who sent it. For that, you would need to find the IP address of the sender. The tutorial below can help you find the IP address of the sender. Note that this will not work if the sender uses anonymous proxy servers.
Finding IP address in Gmail:
1.Log into your Gmail account with your username and password.
2. Open the mail.
3. To display the headers,* Click on More options corresponding to that thread. You should get a bunch of links.* Click on Show original.
4. You should get headers like this:Gmail headers : nameLook for Received: from followed by a few hostnames and an IP address between square brackets. In this case, it is65.119.112.245.That is be the IP address of the sender!
5. Track the IP address of the sender.
How to find the IP address of the sender in Hotmail
Finding IP address in Hotmail
1. Log into your Hotmail account with your username and password.
2. Click on the Mail tab on the top.
3. Open the mail.
4. If you do not see the headers above the mail message, your headers are not displayed. To display the headers,
* Click on Options on the top-right corner
* In the Mail Options page, click on Mail Display Settings
* In Message Headers, make sure Advanced option is checked
* Click on Ok button
* Go back to the mails and open that mail.
5. If you find a header with X-Originating-IP: followed by an IP address, that is the sender's IP addressHotmail headers : name ,In this case the IP address of the sender is [68.34.60.59]. Jump to step 9.
6. If you find a header with Received: from followed by a Gmail proxy like thisHotmail headers : nameLook for Received: from followed by IP address within square brackets[].In this case, the IP address of the sender is [69.140.7.58]. Jump to step 9.
7. Or else if you have headers like thisHotmail headers : nameLook for Received: from followed by IP address within square brackets[].In this case, the IP address of the sender is [61.83.145.129] (Spam mail). Jump to step 9.
8. * If you have multiple Received: from headers, eliminate the ones that have proxy.anyknownserver.com.
9. Track the IP address of the sender
How to find the IP address of the sender in Yahoo! mail
Finding IP address in Yahoo! Mail
1. Log into your Yahoo! mail with your username and password.
2. Click on Inbox or whichever folder you have stored your mail.
3. Open the mail.
4. If you do not see the headers above the mail message, your headers are not displayed. To display the headers,
* Click on Options on the top-right corner
* In the Mail Options page, click on General Preferences
* Scroll down to Messages where you have the Headers option
* Make sure that Show all headers on incoming messages is selected
* Click on the Save button
* Go back to the mails and open that mail.
5. You should see similar headers like this:Yahoo! headers : nameLook for Received: from followed by the IP address between square brackets [ ]. Here, it is 202.65.138.109.That is be the IP address of the sender!
6. Track the IP address of the sender
Recover the lost administrators password in Windows XP
1.First reboot Windows XP in safe mode by re-starting the computer and pressing F8 repeated as the computer starts up.
2.Then (in safe mode) click Start and then click Run. In the open box type "control userpasswords2" without the quotes - I have just used quotes to differentiate what you have to type.
3.You will now have access to all the user accounts, including the administrators account and will be able to reset the lost password.
4.Just click the administrators user account, and then click Reset Password.
5.You will need to add a new password in the New password and the Confirm new password boxes, and confirm by clicking OK.
Keeping the Windows XP Core in the RAM
Go to Start -> Run - Type regedit and press enter - On the left hand side tree, navigate to
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management\
- On the list on the right side, look for an entry called 'DisablePagingExecutive'
- Double click it
- Press 1 on your keyboard
- Click OK
- Exit regedit and reboot the computer
To revert to the default setting, follow the same steps as above, but this time, press 0(zero) instead of 1 on the keyboard.
Remove Thumb.db file
Thumb.db is is a cache of the current picture in that directory.to remove it go for following
step1 > open "WINDOWS EXPLORER".
2>go to "TOOLS".
3>open "FOLDER OPTIONS".
4>go to "VIEW".
5>see 1st section "FILES & FOLDERS".
6>click on the "DO NOT CACHE THUMBNAILS".
now the thumbnail file will be removed from ur computer once u do this the file will be never created.
Error Reporting in XP
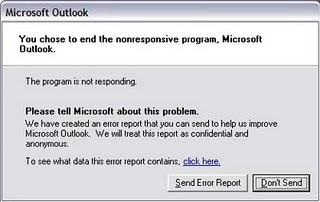
If error reporting in XP is bugging you then turn it off.
When a system error occurs in XP, a little dialog box appears asking if you want to report the error to Microsoft. Click the message box to make it disappear. You don't have to report the error if you don't want to and on today's "Call for Help" Leo shows you how to turn off the feature if you find it distracting.
To disable error reporting, follow these directions:
2. Click the Advanced tab on your System Properties dialog box.
3. Click the Error Reporting button on the Advanced tab.
4. Place a checkmark next to "Disable error reporting."
5. Leave the other radio button unchecked next to the text labeled, "But notify me when critical errors occur."
6. Click OK.
Secret Codes for Nokia
1) *#06# For checking IMEI(international Mobile Equipment Identity)
2) *#7780# Reset to factory settings
3) *#0000# To view software version
4) *#2820# Bluetooth device address
5) *#746025625# Sim clock allowed status
6) #pw+1234567890+1# Shows if ur sim as any restrictions
Tips to recover scratched CD's
2. Then, hold the disc with one hand, use the other to wipe the polish into the affected area with a soft cloth.
3. Wait for it to dry and buff using short, brisk strokes along the scratch, not across it.
4. A cloth sold to wipe spectacles or camera lenses will work super m8's.
5. When you can no longersee the scratch,, wash the disc with water and let it dry before playing. Intersting isnt it? Try it right now
I have used toothpaste with good effects before Ive also used car paint cutting compound on deeper scratches. It does leave lots of smaller scratches (as it is a cutting compound after all) but it will remove the worst scratches in most cases.
ya u r gng to b surely befinited by this Operation
* Fingermarks/prints cause 43% of disc problems!
* General wear & tear causes 25% of disc problems!
* Player-related issues cause 15% of disc problems!
* Remaining Others
Add Your Name (or) Application to right click Of My Computer
As it is related to Windows regisrty it can be dangerous
so,Try This at ur own risk
To write your name on right click application
please follow the steps.
1.Copy/Paste the following code in Notepad And then Save it as .reg
Windows Registry Editor Version 5.00
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\shell\Registry Editor]
@="Your Name Or Name of the Application"
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\shell\Registry Editor\command]
@="Location Of The Application"
2.Now edit it and then Type your name In
Eg:
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\shell\Registry Editor]
@="Rajesh"
3. If u want to get any application, once you click Your name or name of application
Then , Type the location Of the application Which u want to open In:
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\shell\Registry Editor\command]
@="Location Of The Application"
For eg.C:\Program Files\Yahoo!\Messenger\messenger.exe
Thats It finally save it And then Run it .
------------------------------------------------------------
To add Application Control Panel
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\shell\Control Panel\command]
@="rundll32.exe shell32.dll,Control_RunDLL"
To add Application Add/Remove
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\shell\Add/Remove\command]
@="control appwiz.cpl"
To add Application Reboot
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\shell\[Reboot]\command]
@="shutdown -r -f -t 5"
To add Application Shutdown
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\shell\[Shutdown]\command]
@="shutdown -s -f -t 5"
How to "Delete administrator Password" without any software
Boot up with DOS and delete the sam.exe and sam.log files from Windows\system32\config in your hard drive. Now when you boot up in NT the password on your built-in administrator account which will be blank (i.e No password). This solution works only if your hard drive is FAT kind.
Method 2
Step 1. Put your hard disk of your computer in any other pc .
Step 2. Boot that computer and use your hard disk as a secondary hard disk (D'nt boot as primary hard disk ).
Step 3. Then open that drive in which the victim’s window(or your window) is installed.
Step 4. Go to location windows->system32->config
Step 5. And delete SAM.exe and SAM.log
Step 6. Now remove hard disk and put in your computer.
Step 7. And boot your computer :-)
Monday, May 10, 2010
Portable Micro XP 0.82-Launch frm USB stick
Portable Micro XP 0.82[Launch from USB stick in side Windows]
Image - img187. imageshack. us/img187/666/xpusbstckku2. jpg
Description:
This is not a Live CD or USB image. It’s completely portable that you do not require a reboot or cd burning and just run directly from within your windows operating system.
It was created using one of the fastest and slimmest versions of xp ever created by eXperience which is Micro XP 0.82. It has all the benefits of xp sp3 with added patches and security add-ons.
How to run?
Just extract after download
browse through the directory created and click windowsxp.bat.
To transfer file(s):
Share any folder on your current os and also check the option to write files on it.
In the portable version of xp, open explorer and type in the addresss bar
\\10.0.2.2\”shared folder name” - (without quotes)
Some benefits:
1. test any software before you decide to install in your real os.
2. Virus proof as long as you disable folder sharing.
3. run any apps that runs only on xp(assuming you use vista as your primary os)
Tested on both XP Sp3 and Vista x64.
Download - www. megaftp. com/119260
OR
www. mediafire. com/?my2nqi2cmzw
OR
www. megaftp. com/119260
Remove Spaces Between the Links!
Windows 8 Professional Edition
Windows 8 Professional Edition (Leaked Version) | 4.3GB
With Windows 7 poised like a racehorse huffing at the start gate, it's hard to imagine plans for the next version. However, if a leaked roadmap from the Italian Microsoft subsidiary is correct, consumers may see Windows 8 sometimes around 2012. Granted it's easy to doctor a roadmap image using Photoshop and what not, a new OS three years from now certainly isn't unlikely.
This blog points out the tilda next to the date, indicating that Microsoft isn't exactly locked on a 2012 deadline, giving the company some breathing room. "That tilda keeps things nice 'n loose for Microsoft's public deadline, but if Windows 7's development is exemplary of how future versions of Windows are to be developed, (2nd half of) 2012 could be considered a worst-case scenario for the delivery ofWindows 8 Server," the blog reads.
As pointed out by PC Games Hardware, Microsoft's chief of development Steven Sinofsky introduced a method of planning conservative release dates with Windows 7 to prevent another Windows Vista scenario. With that said, Microsoft may internally target an earlier release date with Windows 8.
Hotfile, Easy-Share,Depositfiles Download Links In shorttext. com/h3kamoqk3
Key For The Links Is 1245
Saturday, April 24, 2010
Infected XP owners left unpatched

Infected XP owners left unpatched
|
|
Some of the latest security updates for Windows XP will not be installed on machines infected with a rootkit virus.
A rootkit is sneaky malware that buries itself deep inside the Windows operating system to avoid detection.
Microsoft said it had taken the action because similar updates issued in February made machines infected with the Alureon rootkit crash endlessly.
The latest updates can spot if a system is compromised by the Alureon rootkit and halt installation.
Find and fix
The latest batch of updates for Windows was released on 16 April and some of them fix vulnerabilities in the core, or kernel, of Windows. This is the same place that rootkits try to take up residence.
When Alureon is present it monitors net traffic and plucks out user names, passwords and credit card numbers. It also gives attackers a back door into infected machines.
The virus first appeared in 2008 and has been spread via discussion forums, hacked websites and bogus pay-per-click affiliate schemes.
Notes for the security patch explained which "abnormal conditions" would prevent XP users applying the updates.
"These abnormal conditions on a system could be the result of an infection with a computer virus that modifies some operating system files, which renders the infected computer incompatible with the kernel update," read the statement.
By not applying the patch, Microsoft hopes to avoid a repeat of events in February which left many people struggling to get their computer working again.
Microsoft also wants to avoid a situation in which people become wary of updates because they provoke a crash.
It is not yet clear how many people have been left without the updates.
Microsoft urged those who are infected to ensure their machine is cleaned of the rootkit. It recommended using its malware removal tool or using rootkit detectors from other security companies.
Many modern security packages have them built in and will find rootkits when a machine is scanned.
|
|
Thursday, April 22, 2010
Google's multiple-access pwd s/w hacked
US Internet giant Google's password system that controls multiple access to almost all of its web services was hacked through an innocuous message sent to a Google employee in China, a media report said Tuesday.
Though Google had disclosed in January that intruders had stolen information from its computers in the cyber attack in December 2009, the extent of the theft has been a closely guarded company secret till now.
The programme, code named "Gaia" for the Greek goddess of the earth, was attacked in December, a source close to the investigation was quoted as saying by New York Times Tuesday.
It is intended to enable multiple access to users and employees, who can sign in with their password just once to operate a range of services.
Though Google quickly started making significant changes to the security of its networks after the intrusions, the theft has left open the possibility that the intruders may find weaknesses that the company might not even be aware of.
The theft began with a message sent to a Google employee in China who was using Microsoft's Messenger programme at that time. By clicking on a link and connecting to a "poisoned" website, the employee inadvertently permitted the intruders to gain access to his computer and then to the computers of a critical group of software developers at Google's headquarters in California.
The details of the theft have been a closely guarded secret. Google first publicly disclosed the theft January 12, 2010, on the company's website, which said the company was changing its policy towards China in the wake of the theft of unidentified "intellectual property".
This led to significant tension between the US and China, leading Secretary of State Hillary Clinton to urge China to conduct a "transparent" inquiry into the matter. In March, after discussions with the Chinese government, Google re-routed its mainland Chinese-language website to its Hong Kong-based site.
Google continues to use the Gaia system, now known as "Single Sign-On". The company also tightened security of its data centres and further secured the communication links between its services and the computers of its users.
However, having access to the original programmer's instructions, or source code, could also provide technically skilled hackers with knowledge about subtle security vulnerabilities in the programme that may have eluded Google's engineers.
"If you can get to the software repository where the bugs are housed before they are patched, that's the pot of gold at the end of the rainbow," George Kurtz, chief technology officer for McAfee Inc, was quoted as saying.
McAfee Inc was one of the companies that analysed the illicit software used in the intrusions at Google and at other companies last year.
When Google first announced the theft, it said it had evidence that the intrusions had come from China. The attacks have been traced to computers at two campuses in China, but investigators later said the true origin may have been concealed.
Friday, February 26, 2010
Run Commands in Windows XP
You can access all these programs by going through START-->RUN or Simply Click Windows Key+R
SQL Client Configuration - cliconfg
System Configuration Editor - sysedit
System Configuration Utility - msconfig
System File Checker Utility (Scan Immediately)- sfc /scannow
System File Checker Utility (Scan Once At Next Boot)- sfc /scanonce
System File Checker Utility (Scan On Every Boot) - sfc /scanboot
System File Checker Utility (Return to Default Setting)- sfc /revert
System File Checker Utility (Purge File Cache)- sfc /purgecache
System File Checker Utility (Set Cache Size to size x)-sfc/cachesize=x
System Information - msinfo32.
Task Manager – taskmgr
System Properties - sysdm.cpl
Task Manager – taskmgr
TCP Tester - tcptest
Telnet Client - telnet
Tweak UI (if installed) - tweakui
User Account Management- nusrmgr.cpl
Utility Manager - utilman
Windows Address Book - wab
Windows Address Book Import Utility - wabmig
Windows Backup Utility (if installed)- ntbackup
Windows Explorer - explorer
Windows Firewall- firewall.cpl
Windows Magnifier- magnify
Windows Management Infrastructure - wmimgmt.msc
Windows Media Player - wmplayer
Windows Messenger - msmsgs
Windows Picture Import Wizard (need camera connected)- wiaacmgr
Windows System Security Tool – syskey
Windows Update Launches - wupdmgr
Windows Version (to show which version of windows)- winver
Windows XP Tour Wizard - tourstart
Wordpad - write
Password Properties - password.cpl
Performance Monitor - perfmon.msc
Phone and Modem Options - telephon.cpl
Phone Dialer - dialer
Pinball Game - pinball
Power Configuration - powercfg.cpl
Printers and Faxes - control printers
Printers Folder – printers
Private Character Editor - eudcedit
Quicktime (If Installed)- QuickTime.cpl
Real Player (if installed)- realplay
Regional Settings - intl.cpl
Registry Editor - regedit
Registry Editor - regedit32
Remote Access Phonebook - rasphone
Remote Desktop - mstsc
Removable Storage - ntmsmgr.msc
Removable Storage Operator Requests - ntmsoprq.msc
Resultant Set of Policy (XP Prof) - rsop.msc
Scanners and Cameras - sticpl.cpl
Scheduled Tasks - control schedtasks
Security Center - wscui.cpl
Services - services.msc
Shared Folders - fsmgmt.msc
Shuts Down Windows - shutdown
Sounds and Audio - mmsys.cpl
Spider Solitare Card Game - spider
Malicious Software Removal Tool - mrt
Microsoft Access (if installed) - access.cpl
Microsoft Chat - winchat
Microsoft Excel (if installed) - excel
Microsoft Frontpage (if installed)- frontpg
Microsoft Movie Maker - moviemk
Microsoft Paint - mspaint
Microsoft Powerpoint (if installed)- powerpnt
Microsoft Word (if installed)- winword
Microsoft Syncronization Tool - mobsync
Minesweeper Game - winmine
Mouse Properties - control mouse
Mouse Properties - main.cpl
Nero (if installed)- nero
Netmeeting - conf
Network Connections - control netconnections
Network Connections - ncpa.cpl
Network Setup Wizard - netsetup.cpl
Notepad - notepad
Nview Desktop Manager (If Installed)- nvtuicpl.cpl
Object Packager - packager
ODBC Data Source Administrator- odbccp32.cpl
On Screen Keyboard - osk
Opens AC3 Filter (If Installed) - ac3filter.cpl
Outlook Express - msimn
Paint – pbrush
Keyboard Properties - control keyboard
IP Configuration (Display Connection Configuration) - ipconfi/all
IP Configuration (Display DNS Cache Contents)- ipconfig /displaydns
IP Configuration (Delete DNS Cache Contents)- ipconfig /flushdns
IP Configuration (Release All Connections)- ipconfig /release
IP Configuration (Renew All Connections)- ipconfig /renew
IP Configuration(RefreshesDHCP&Re-RegistersDNS)-ipconfig/registerdns
IP Configuration (Display DHCP Class ID)- ipconfig/showclassid
IP Configuration (Modifies DHCP Class ID)- ipconfig /setclassid
Java Control Panel (If Installed)- jpicpl32.cpl
Java Control Panel (If Installed)- javaws
Local Security Settings - secpol.msc
Local Users and Groups - lusrmgr.msc
Logs You Out Of Windows - logoff.....
Accessibility Controls - access.cpl
Accessibility Wizard - accwiz
Add Hardware - Wizardhdwwiz.cpl
Add/Remove Programs - appwiz.cpl
Administrative Tools control - admintools
Adobe Acrobat (if installed) - acrobat
Adobe Designer (if installed)- acrodist
Adobe Distiller (if installed)- acrodist
Adobe ImageReady (if installed)- imageready
Adobe Photoshop (if installed)- photoshop
Automatic Updates - wuaucpl.cpl
Bluetooth Transfer Wizard – fsquirt
Calculator - calc
Certificate Manager - certmgr.msc
Character Map - charmap
Check Disk Utility - chkdsk
Clipboard Viewer - clipbrd
Command Prompt - cmd
Component Services - dcomcnfg
Computer Management - compmgmt.msc
Control Panel - control
Date and Time Properties - timedate.cpl
DDE Shares - ddeshare
Device Manager - devmgmt.msc
Direct X Control Panel (If Installed)- directx.cpl
Direct X Troubleshooter- dxdiag
Disk Cleanup Utility- cleanmgr
Disk Defragment- dfrg.msc
Disk Management- diskmgmt.msc
Disk Partition Manager- diskpart
Display Properties- control desktop
Display Properties- desk.cpl
Display Properties (w/Appearance Tab Preselected)- control color
Dr. Watson System Troubleshooting Utility- drwtsn32
Driver Verifier Utility- verifier
Event Viewer- eventvwr.msc
Files and Settings Transfer Tool- migwiz
File Signature Verification Tool- sigverif
Findfast- findfast.cpl
Firefox (if installed)- firefox
Folders Properties- control folders
Fonts- control fonts
Fonts Folder- fonts
Free Cell Card Game- freecell
Game Controllers- joy.cpl
Group Policy Editor (XP Prof)- gpedit.msc
Hearts Card Game- mshearts
Help and Support- helpctr
HyperTerminal- hypertrm
Iexpress Wizard- iexpress
Indexing Service- ciadv.msc
Internet Connection Wizard- icwconn1
Internet Explorer- iexplore
Internet Setup Wizard- inetwiz
Internet Properties- inetcpl.cpl
REGEDIT Keyboard Shortcuts
"Ctrl+F" -- Opens the Find dialog box.
"F3" -- Repeats the last search.
Browsing:
"Keypad +" -- Expands the selected branch.
"Keypad -" -- Collapses the selected branch.
"Keypad *" -- Expands all the selected branch's sub keys.
"Up Arrow" -- Selects the previous key.
"Down Arrow" -- Selects the next key.
"Left Arrow" -- Collapses the selected branch if it's not collapsed; otherwise, selects the parent key.
"Right Arrow" -- Expands the selected branch if it's not already expanded; otherwise, selects the key's first sub key.
"Home" -- Selects My Computer.
"End" -- Selects the last key that's visible in the key pane.
"Page Up" -- Moves up one page in the key pane.
"Page Down" -- Moves down one page in the key pane.
"Tab" -- Moves between the key and value panes.
"F6" -- Moves between the key and value panes.
Others:
"Delete" -- Deletes the select branch or value.
"F1" -- Opens Regedit's Help.
"F2" -- Renames the selected key or value.
"F5" -- Refreshes the key and value panes.
"F10" -- Opens Regedit's menu bar.
"Shift+F10" -- Opens the shortcut menu for the selected key or value.
"Alt+F4" -- Closes Regedit.
Enable virtual Wi-Fi in windows 7
Enable virtual Wi-Fi in Windows 7….
Windows 7 includes a little-known new feature called Virtual Wi-Fi, which effectively turns your PC or laptop into a software-based router. Any other Wi-Fi-enabled devices within range - a desktop, laptop, an iPod perhaps - will "see" you as a new network and, once logged on, immediately be able to share your internet connection.
This will only work if your wireless adapter driver supports it, though, and not all do. Check with your adapter manufacturer and make sure you've installed the very latest drivers to give you the best chance.
Once you have driver support then the easiest approach is to get a network tool that can set up virtual Wi-Fi for you. Virtual Router (below) is free, easy to use and should have you sharing your internet connection very quickly.
If you don't mind working with the command line, though, maybe setting up some batch files or scripts, then it's not that difficult to set this up manually. See Turn your Windows 7 laptop into a wireless hotspot for more.
How to Put Google Adsense Below Post Title in Blogger?
Adsense is used by majority of expert bloggers for their website monetization because it is a cookie based contextual advertising syste...

-
Adsense is used by majority of expert bloggers for their website monetization because it is a cookie based contextual advertising syste...
-
Portable Micro XP 0.82[Launch from USB stick in side Windows] Image - img187. imageshack. us/img187/666/xpusbstckku2. jpg Descriptio...
-
Change the Default Directory of Software Installation You may want to change the location of your system default folder (C:\Program Files) f...
